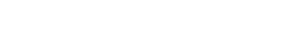Logging in to a website is something that an ordinary Internet user would not give a second thought. But imagine that you work in a big enterprise and you have dozens of systems to log in. If you want to reduce the administrative burden and ensure proper authentication for your employees, consider implementation of the Single Sign-On authentication capability provided by Quintagroup. This technology will raise to a whole new level your company's security and management and your employees' productivity. In our tutorial, we use SAML (Security Assertion Markup Language) to integrate the Single Sign-On (SSO) authentication via Google/GitHub account in Plone with Auth0.
Single Sign-On
SSO (Single Sign-On) is the technology of unified authentication. It provides users with the ability to enter login information once and be authenticated to multiple applications within an enterprise. Regardless of the platform, technology, or domain, the SSO system will keep your credentials recorded after logging into one of the applications. This means you don’t need to enter your identification information like username and password when entering other platforms. The seamless authentication experience provided by the Single Sign-On technology prevents your internal employees and external users from the big hassle of maintaining and remembering yet another credential.
To turn this technology into reality, Quintagroup used Auth0 as a central server for the SSO solution.
Auth0 Overview
Auth0 is a provider of authentication and authorization as a service. In plain words, Auth0 is like the universal dongle that simplifies the connection of multiple devices with your laptop or computer. But in our case, Auth0 simplifies connection of multiple identity sources with your app or website.
Auth0 application areas are vast and wide. It can be used for:
- implementation of the Single Sign-On system (SSO);
- implementation of your own user management solution if you need password resets, creating, provisioning, blocking and deleting users, and the UI management;
- analytics of tracking users on your site or application. This data can be used to create funnels, measure user retention, and improve your sign-up flow;
- blocking suspicious IP addresses that make consecutive failed login attempts, in order to avoid DDoS attacks.
In order to design an authentication and authorization systems, Auth0 uses a set of open specifications and protocols. The list of compatible with Auth0 identity standards that control identity, move personal data, and decide who can access applications include Open Authorization (OAuth), OpenID Connect (OIDC), JSON Web Tokens (JWT) and Security Assertion Markup Language (SAML2). In our case, the last one was used for an SSO authentication via Google/GitHub account in Plone.
SAML2
Developed by OASIS, SAML2 is an advanced variant and a current version of the Security Assertion Markup Language that was established in 2005. SAML is an XML-based standard that allows security functions to pass information about a user.
SAML is frequently the underlying protocol that makes web-based SSO possible. It enables a company to maintain a single login page and allows users to log into all web apps from the same login screen with a single set of credentials. The process of obtaining access to the website is conducted by the SAML authorities.
SAML authorities
The role of SAML authorities is performed by two SAML providers: the service provider (SP) and the identity provider (IdP). For our tutorial, we have chosen Plone as the Service Provider and Auth0 as the Identity Provider.
In the use case addressed by SAML, the user agent requests a service from the SP. The SP requests and obtains an authentication assertion from the IdP. Based on this assertion, the SP makes an access control decision — in other words, it decides whether to run some services for the connected user agent. SAML does not specify the method of authentication at the IdP; it may require a username and password, or another form of authentication.
SAML components
Assertions, protocol, binding, and profile - these are the components SAML requests and responses are constructed from.
Assertions – An assertion is a package of information about the user provided by a SAML authority and packed as an XML document. SAML defines three different types of SAML Assertions – authentication, attribute, and authorization decision.
- Authentication assertions prove that the users are who they claim to be.
- Attribute assertions supply specific pieces of data about the users, for example, their email address or phone number.
- Authorization decisions determine whether the user is authorized to access the specified resource.
Protocol – This is the way SAML requests and gets assertions.
Profile – A SAML profile describes in detail how SAML assertions, protocols, and bindings combine to support a defined use case. The most important SAML profile is the Web Browser SSO Profile.
What is the use of it?
Implementation of the following demo into your enterprise authentication system or the use of SSO authentication has a number of benefits.
Improved usability |
Top security |
Effortless management |
||
|
Remembering separate usernames and passwords for each app may result in a huge cognitive burden for your employees. Taking this burden off their shoulders will save their time and improve their productivity. Your employees will no longer need to switch between dozens of apps every hour without specifying their credentials each time. |
Reducing login to one set of credentials improves enterprise security. When employees have to use separate passwords for each app, they usually don’t. In fact, the majority use the same or similar passwords on multiple accounts. Thus, if a hacker gets access through one poorly secured website, they are likely to be able to access other corporate systems. |
|
TUTORIAL
And now, when you know the basics of the SSO, SAML, and Auth0, don’t test the water, jump right into the pool of technological experience and use our tutorial as the swimming armbands to stay safe and sound.
Please note that in our tutorial we use
- “qg-dev.auth0.com” as our auth0 tenant name and
- “plone-saml-demo.office.quintagroup.com” as our Plone demo website FQDN.
So make sure to substitute them with your own values.
Auth0
Configure Social Connections
Use the following guides to enable login with Google and GitHub accounts to your website:
Also, ensure that Auth0 dev keys aren't used since the Plone SAML2 plugin doesn't accept responses via a redirect.
Create Application
- Login to Auth0 dashboard
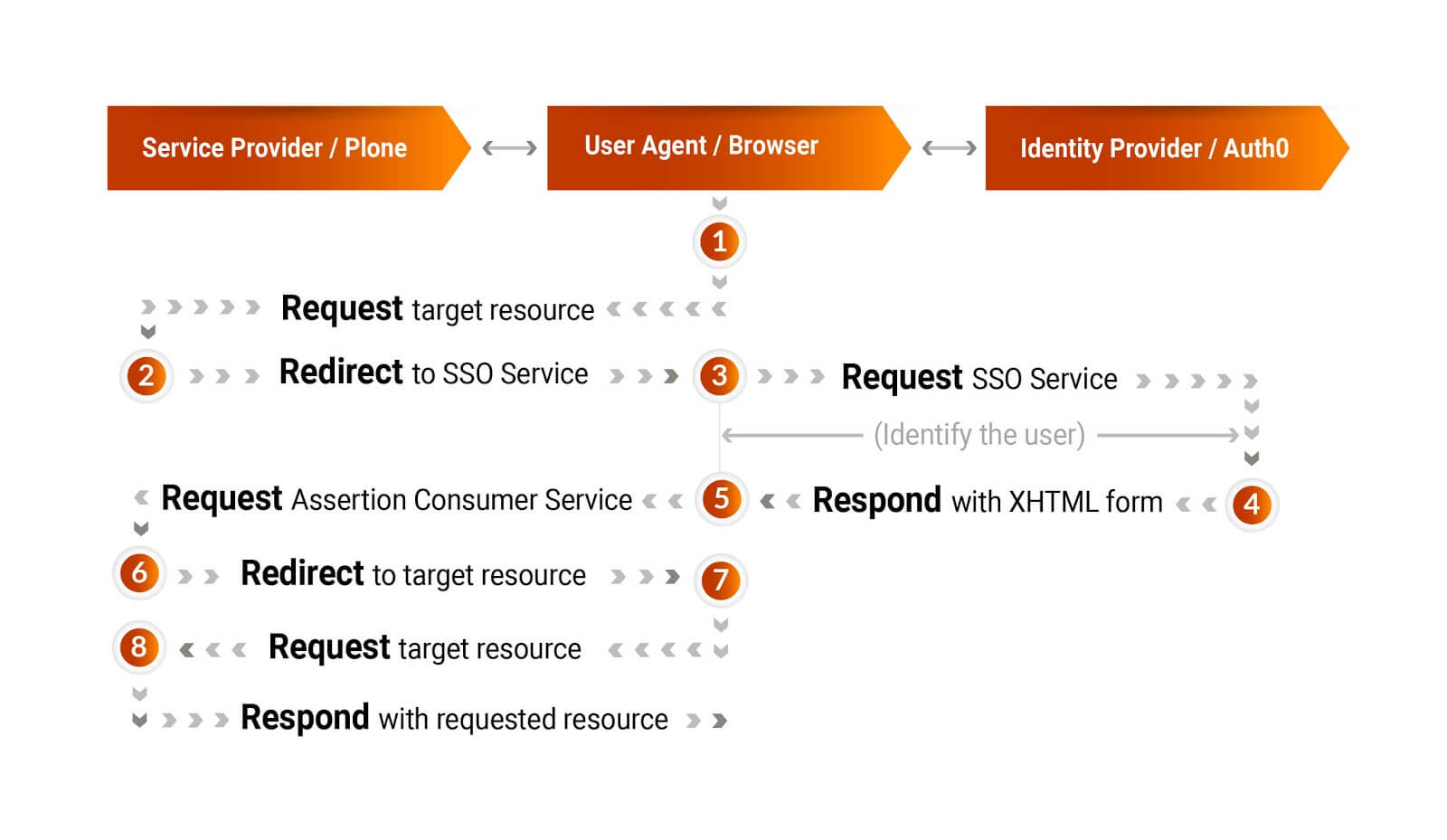
- Navigate to the Applications section and click Create application with the following values:
- Name: Plone SAML2 Demo
- Type: Regular Web Application type
Configure Auth0 as a SAML2 Identity Provider (IdP)
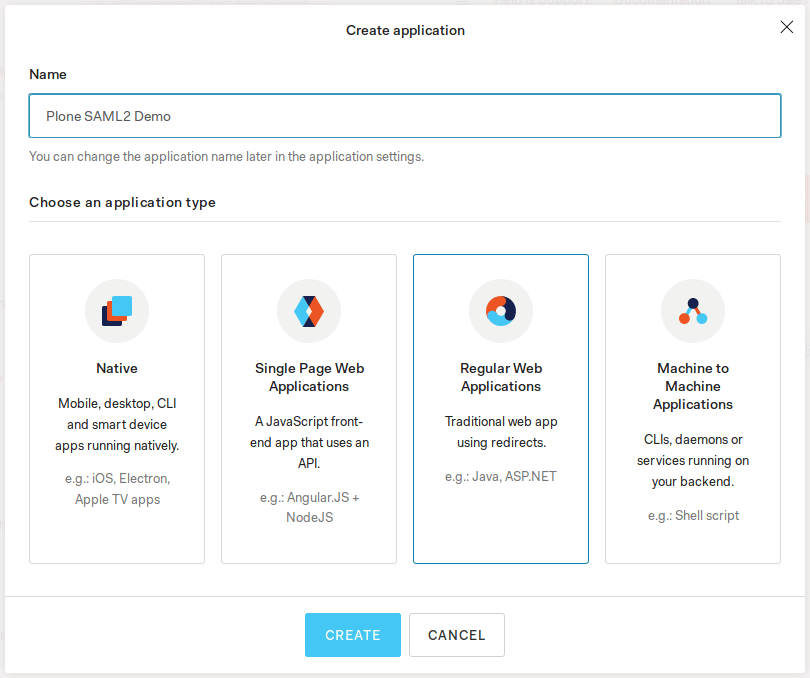
- Select your newly created application and switch to the Addons tab.
- Enable SAML2 Web App addon.
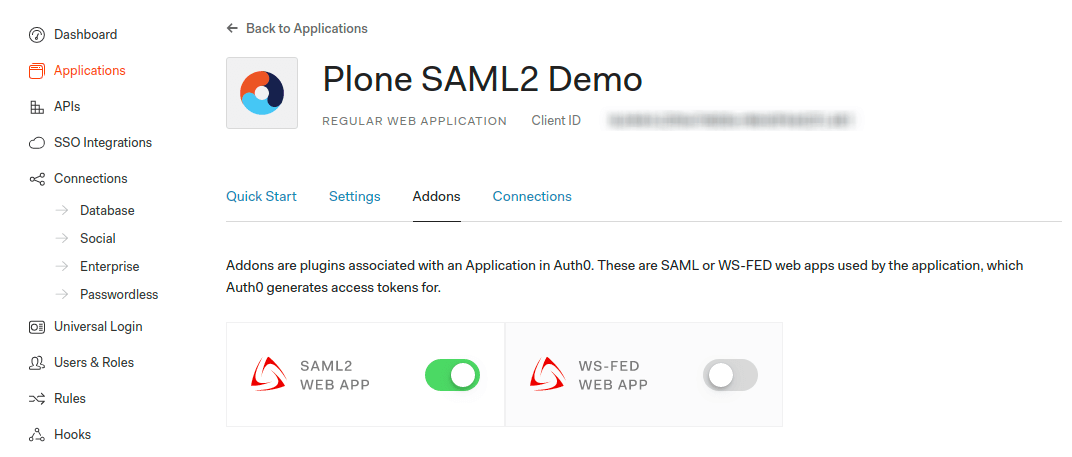
3. On the Settings tab set the Application Callback URL to https://plone-saml-demo.office.quintagroup.com/acl_users/saml2sp/post and click Enable.
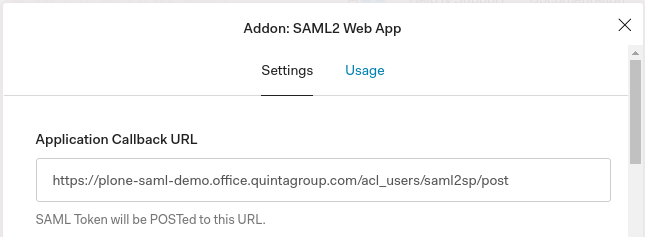
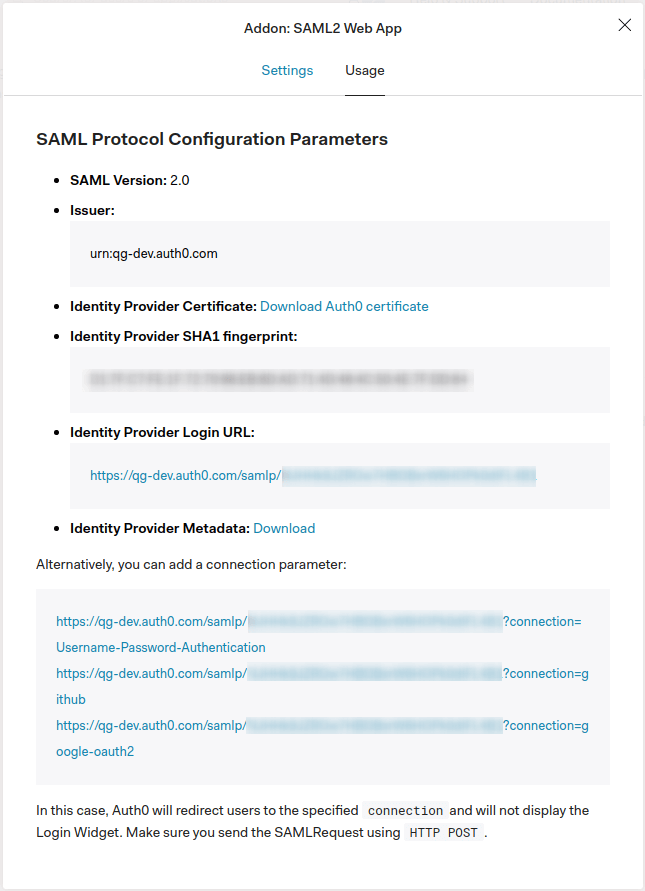
4. On the Usage tab save the Issuer value (e.g. urn:qg-dev.auth0.com) and Identity Provider Metadata download URL (https://qg-dev.auth0.com/samlp/metadata/<AUTH0_APP_CLIENT_ID>).
PLONE
First things first, you need to install Plone using minimal buildout. We recommend using our buildout.cfg file that can be found on Github that already includes dm.zope.saml2 plugin.
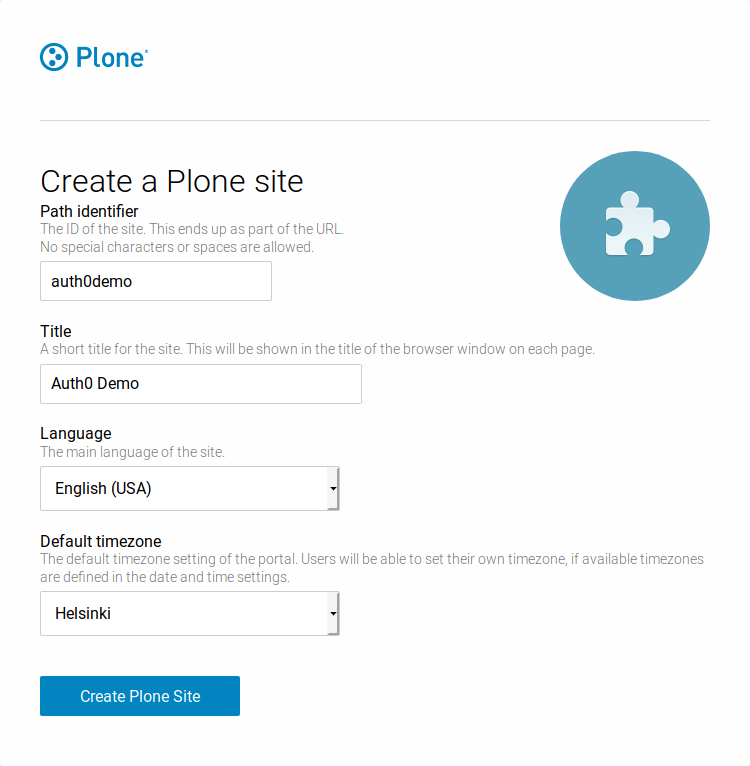
- In this demo, we will create a new Plone site with the path identifier set to auth0demo
2. Configure your proxy server to map requests to the auth0demo Plone site. Example configuration for nginx (or see it on Github):
server {
listen 80 default_server;
listen [::]:80 default_server;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name plone-saml-demo.office.quintagroup.com;
ssl_certificate /etc/pki/tls/certs/plone-saml-demo.office.quintagroup.com.crt;
ssl_certificate_key /etc/pki/tls/private/plone-saml-demo.office.quintagroup.com.key;
access_log /var/log/nginx/plone-saml-demo.log;
error_log /var/log/nginx/plone-saml-demo_error.log;
location / {
proxy_pass http://127.0.0.1:8080/VirtualHostBase/https/$host:443/auth0demo/VirtualHostRoot/$request_uri;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
Create SAML2 authority
- Navigate to the Management interface (admin -> Site Setup -> Advanced -> Management Interface)
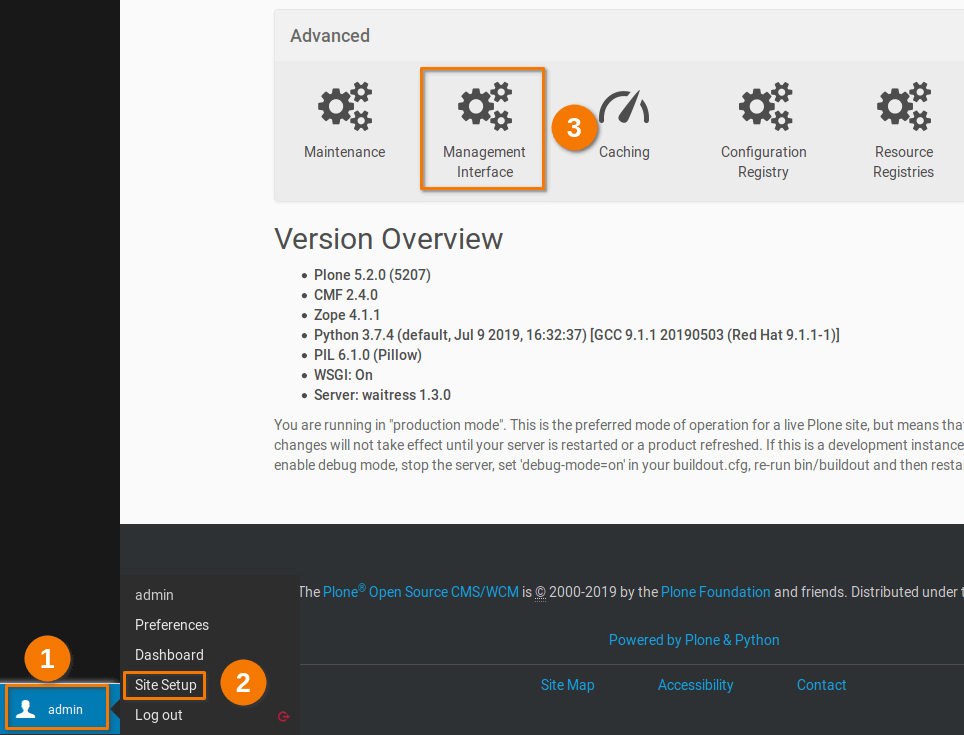
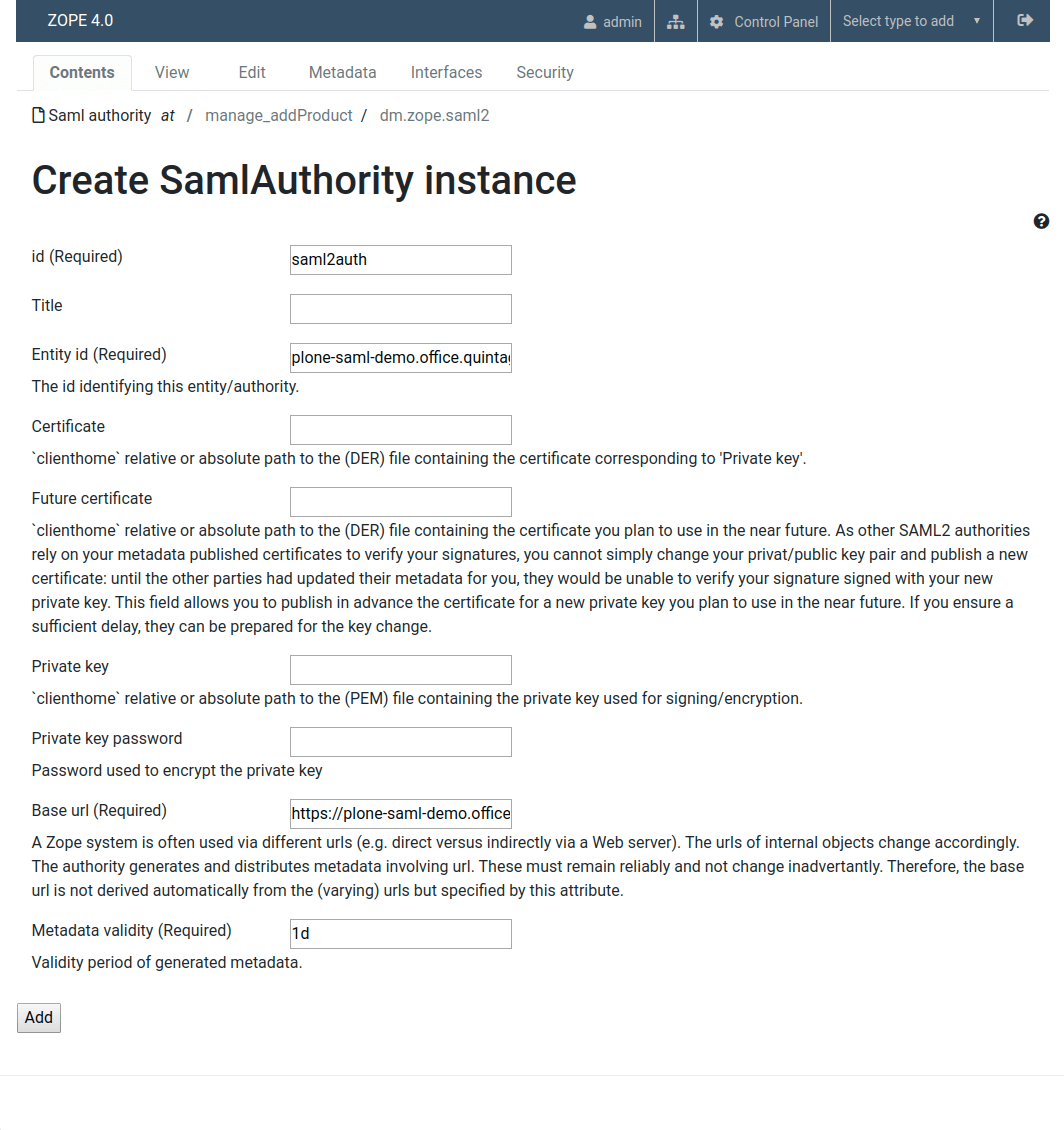
2. At the root of a Plone site add Saml authority with the following values:
- Id: saml2auth
- Entity Id: plone-saml-demo.office.quintagroup.com/saml2auth/metadata
- Base url: https://plone-saml-demo.office.quintagroup.com
Configure Plone as a SAML2 Service Provider (SP)
- At the root of a Plone site go to the acl_users
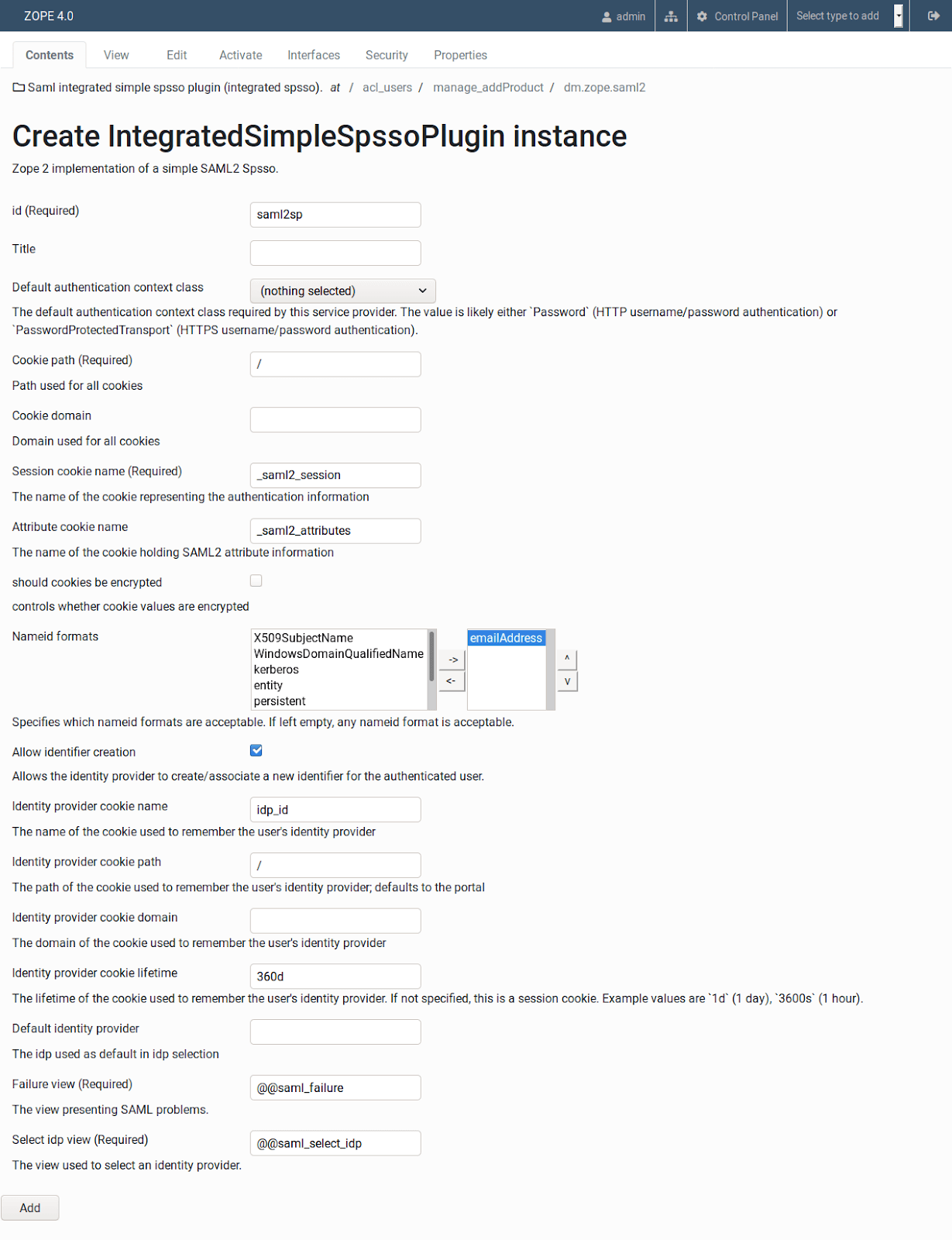
- Add Saml integrated simple spsso plugin (integrated spsso) with the following values:
- Id: saml2sp
- Nameid formats: emailAddress
3. Go to the Activate tab and enable all plugins
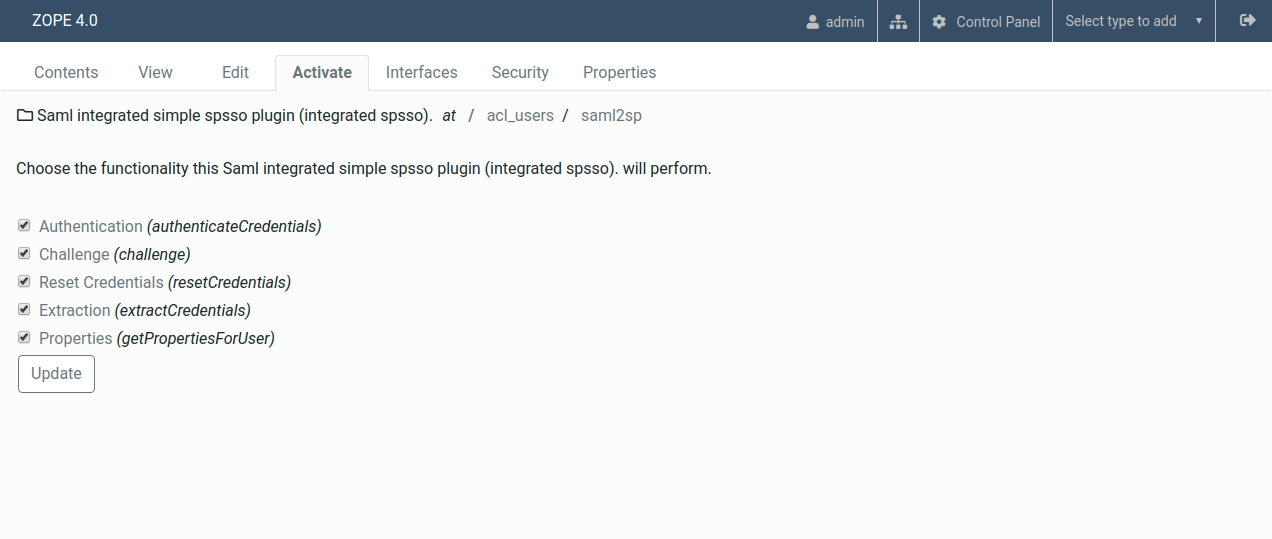
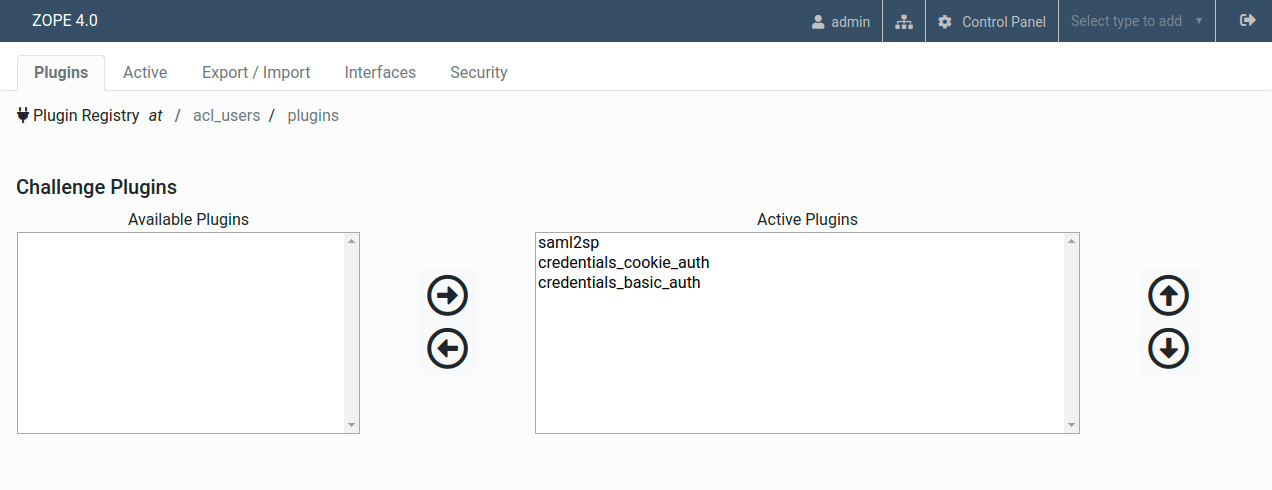
4. Go to the Activate tab and click on the Challenge plugin
5. Ensure that saml2sp is at the top of the Active Plugins list
Add Auth0 IdP metadata
- At the root of a Plone site go to the saml2auth
- Add Saml2 entity defined by metadata providing url with the values from the step 4 of Configure Auth0 as a SAML2 Identity Provider (IdP):
- Id: Issuer
- Url: Identity Provider Metadata download URL
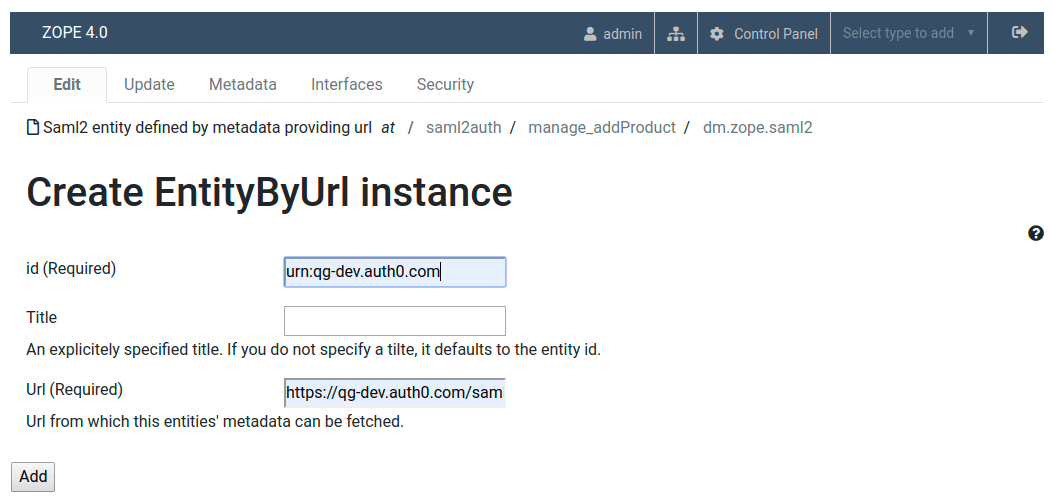
Now you can test if SAML2 Single Sign-On is working by going to the https://plone-saml-demo.office.quintagroup.com/acl_users/saml2sp/login link.
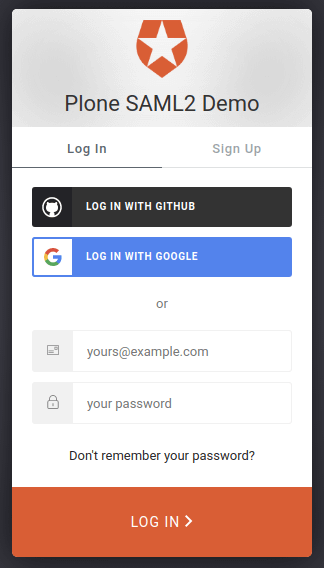
If you see the Auth0 login prompt as on the picture above - congratulations! You've successfully enabled SAML2 authentication on your Plone website.
This is not the end
SSO authentication is not the only possible application of the SAML and Auth0 combination. Well-rounded technological solutions delivered by Quintagroup may also include
- User or group mapping
- Defining user roles
- User group membership
- Extraction of the user profile information from SAML Attribute Assertions (e.g., username and email)
Feel inspired by our article? Let us know and maybe you will be the next lucky client of Quintagroup. And now, this is the end of the article.